The meaning and identification of php verification code
This article mainly introduces the meaning and identification of PHP verification code. Interested friends can refer to it. I hope it will be helpful to everyone.
Verification code
Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHA for short), commonly known as verification code, is a public automatic program that distinguishes users as computers and humans. In a CAPTCHA test, the computer as the server automatically generates a question for the user to answer. This question can be generated and judged by a computer, but only a human can answer it. Since computers cannot answer CAPTCHA questions, the user who answers the questions can be considered a human.
Encyclopedia Introduction
To put it simply, it is randomly generated characters and output on a picture [other forms of drag and drop/SMS verification codes, etc. are not considered here].
Common types

Ideas
This article is for demonstration only, so the first picture verification code is taken As an example to explain.
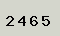
Every point on the picture has its RGB value, which can be obtained through the color picker. It can be seen with the naked eye that the verification code of the picture is a pure digital solid color. Background
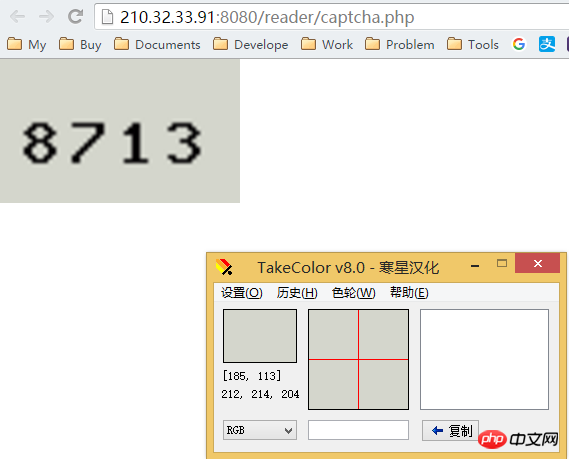
It can be seen through the color picker that the background color RGB value of the verification code is (212,214,204)
Implementation
Let’s use PHP’s imagecolorsforindex function to obtain the RGB values of all points in the image:
$url = 'http://210.32.33.91:8080/reader/captcha.php';
$im = imagecreatefromgif($url);
imagegif($im, '1.gif');
$rgbArray = array();
$res = $im;
$size = getimagesize($url);
$wid = $size['0'];
$hid = $size['1'];
for ($i = 0; $i < $hid; ++ $i) {
for ($j = 0; $j < $wid; ++ $j) {
$rgb = imagecolorat($res, $j, $i);
$rgbArray[$i][$j] = imagecolorsforindex($res, $rgb);
}
}Result As follows:
You may want to ask what is the use of this? Let's display the data in another way, output □ for the background color, and verify Code area output ■, let’s look at it again:
for ($i = 0; $i < $hid; $i ++) {
for ($j = 0; $j < $wid; $j ++) {
if ($rgbArray[$i][$j]['red'] == 212) {
echo '□';
} else {
echo '■';
}
}
echo "<br>";
} Effect:
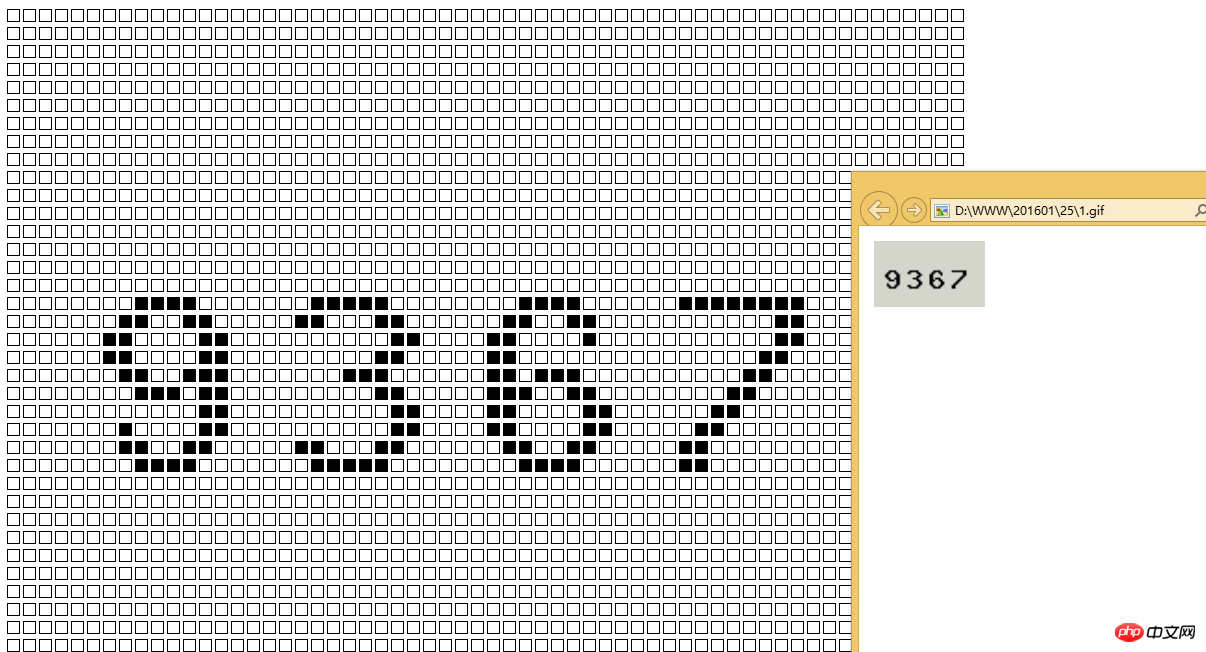
Is it clear now?
But you may still have questions. Although you can see it, how do you know how much it is?
Let’s analyze it below:

The distance between each verification code is 4 spaces, the left and right spacing is 6/10 spaces, and the top and bottom spacing is 16/10 spaces.
Let’s remove these interference points again so that we can see more clearly:
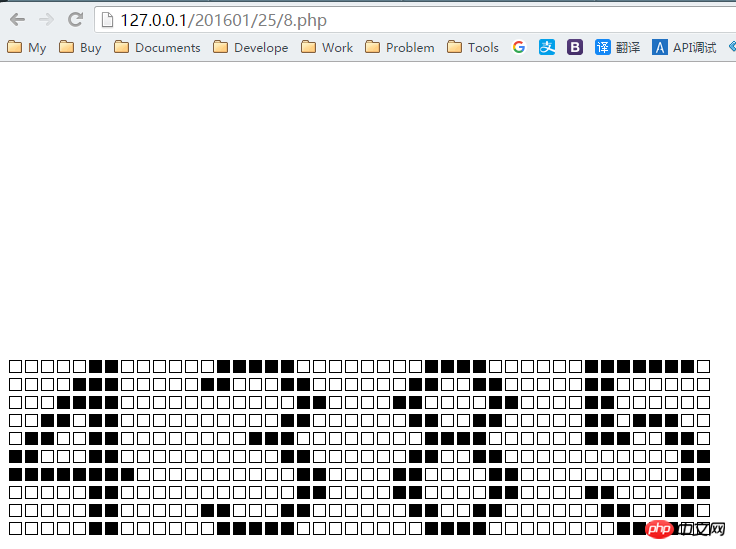
Is it very clear? There may still be someone there I will ask, how can you know what the numbers on the picture are after you have talked so much.
Okay, let me tell you my thoughts. Let’s combine the □ and ■ Replace with 0 and 1, and the shapes of these numbers are fixed, so you can get that every area 8*10 of each word from 0-9 is composed of 0 and 1,

Let’s do every 8 segments again, remove the 4-space spacing, and loop to get the 01 combination value of 0-9:

##
$dic = array( '00011000001111000110011011000011110000111100001111000011011001100011110000011000' => 0, '00011000001110000111100000011000000110000001100000011000000110000001100001111110' => 1, '00111100011001101100001100000011000001100000110000011000001100000110000011111111' => 2, '01111100110001100000001100000110000111000000011000000011000000111100011001111100' => 3, '00000110000011100001111000110110011001101100011011111111000001100000011000000110' => 4, '11111110110000001100000011011100111001100000001100000011110000110110011000111100' => 5, '00111100011001101100001011000000110111001110011011000011110000110110011000111100' => 6, '11111111000000110000001100000110000011000001100000110000011000001100000011000000' => 7, '00111100011001101100001101100110001111000110011011000011110000110110011000111100' => 8, '00111100011001101100001111000011011001110011101100000011010000110110011000111100' => 9 );


##Summary: The above is the entire content of this article, I hope it will be helpful to everyone's study.
Related recommendations:
PHPExcel implementation of reading excel files and simple examplesPHP MVC framework skymvc supports multiple file upload implementation methodsA simple analysis of confusing length calculation issues in PHP
##
The above is the detailed content of The meaning and identification of php verification code. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1658
1658
 14
14
 1415
1415
 52
52
 1309
1309
 25
25
 1257
1257
 29
29
 1231
1231
 24
24
 How does session hijacking work and how can you mitigate it in PHP?
Apr 06, 2025 am 12:02 AM
How does session hijacking work and how can you mitigate it in PHP?
Apr 06, 2025 am 12:02 AM
Session hijacking can be achieved through the following steps: 1. Obtain the session ID, 2. Use the session ID, 3. Keep the session active. The methods to prevent session hijacking in PHP include: 1. Use the session_regenerate_id() function to regenerate the session ID, 2. Store session data through the database, 3. Ensure that all session data is transmitted through HTTPS.
 Explain different error types in PHP (Notice, Warning, Fatal Error, Parse Error).
Apr 08, 2025 am 12:03 AM
Explain different error types in PHP (Notice, Warning, Fatal Error, Parse Error).
Apr 08, 2025 am 12:03 AM
There are four main error types in PHP: 1.Notice: the slightest, will not interrupt the program, such as accessing undefined variables; 2. Warning: serious than Notice, will not terminate the program, such as containing no files; 3. FatalError: the most serious, will terminate the program, such as calling no function; 4. ParseError: syntax error, will prevent the program from being executed, such as forgetting to add the end tag.
 PHP and Python: Comparing Two Popular Programming Languages
Apr 14, 2025 am 12:13 AM
PHP and Python: Comparing Two Popular Programming Languages
Apr 14, 2025 am 12:13 AM
PHP and Python each have their own advantages, and choose according to project requirements. 1.PHP is suitable for web development, especially for rapid development and maintenance of websites. 2. Python is suitable for data science, machine learning and artificial intelligence, with concise syntax and suitable for beginners.
 Explain secure password hashing in PHP (e.g., password_hash, password_verify). Why not use MD5 or SHA1?
Apr 17, 2025 am 12:06 AM
Explain secure password hashing in PHP (e.g., password_hash, password_verify). Why not use MD5 or SHA1?
Apr 17, 2025 am 12:06 AM
In PHP, password_hash and password_verify functions should be used to implement secure password hashing, and MD5 or SHA1 should not be used. 1) password_hash generates a hash containing salt values to enhance security. 2) Password_verify verify password and ensure security by comparing hash values. 3) MD5 and SHA1 are vulnerable and lack salt values, and are not suitable for modern password security.
 What are HTTP request methods (GET, POST, PUT, DELETE, etc.) and when should each be used?
Apr 09, 2025 am 12:09 AM
What are HTTP request methods (GET, POST, PUT, DELETE, etc.) and when should each be used?
Apr 09, 2025 am 12:09 AM
HTTP request methods include GET, POST, PUT and DELETE, which are used to obtain, submit, update and delete resources respectively. 1. The GET method is used to obtain resources and is suitable for read operations. 2. The POST method is used to submit data and is often used to create new resources. 3. The PUT method is used to update resources and is suitable for complete updates. 4. The DELETE method is used to delete resources and is suitable for deletion operations.
 PHP: A Key Language for Web Development
Apr 13, 2025 am 12:08 AM
PHP: A Key Language for Web Development
Apr 13, 2025 am 12:08 AM
PHP is a scripting language widely used on the server side, especially suitable for web development. 1.PHP can embed HTML, process HTTP requests and responses, and supports a variety of databases. 2.PHP is used to generate dynamic web content, process form data, access databases, etc., with strong community support and open source resources. 3. PHP is an interpreted language, and the execution process includes lexical analysis, grammatical analysis, compilation and execution. 4.PHP can be combined with MySQL for advanced applications such as user registration systems. 5. When debugging PHP, you can use functions such as error_reporting() and var_dump(). 6. Optimize PHP code to use caching mechanisms, optimize database queries and use built-in functions. 7
 Explain Arrow Functions (short closures) introduced in PHP 7.4.
Apr 06, 2025 am 12:01 AM
Explain Arrow Functions (short closures) introduced in PHP 7.4.
Apr 06, 2025 am 12:01 AM
The arrow function was introduced in PHP7.4 and is a simplified form of short closures. 1) They are defined using the => operator, omitting function and use keywords. 2) The arrow function automatically captures the current scope variable without the use keyword. 3) They are often used in callback functions and short calculations to improve code simplicity and readability.
 PHP in Action: Real-World Examples and Applications
Apr 14, 2025 am 12:19 AM
PHP in Action: Real-World Examples and Applications
Apr 14, 2025 am 12:19 AM
PHP is widely used in e-commerce, content management systems and API development. 1) E-commerce: used for shopping cart function and payment processing. 2) Content management system: used for dynamic content generation and user management. 3) API development: used for RESTful API development and API security. Through performance optimization and best practices, the efficiency and maintainability of PHP applications are improved.




