Java authorization and authentication
CRMPermission management
1. Concept
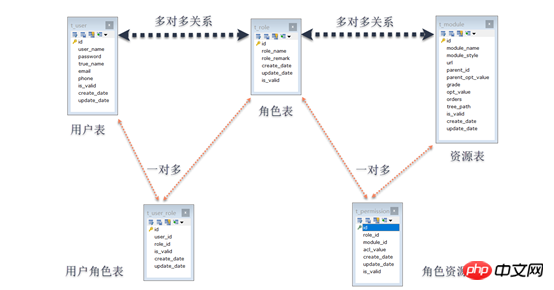
Permission management is to manage user operations on resources. The Permissions (also called resources) of this CRM system are implemented based on role operation permissions, that is, RBAC (Role-Based Access Control, role-based access control), which means that users are associated with permissions through roles. . Simply put, a user has several roles, and each role has several permissions. In this way, a "user-role-permission" authorization model is constructed. In this model, there is a many-to-many relationship between users and roles, and between roles and permissions. In order to realize the many-to-many relationship between tables, a many-to-many relationship must be divided into Two-to-many relationship. Therefore, intermediate tables, user role tables and role permission tables are introduced.
2. Database
The authority management module involves a total offive tables:
Three main tables
a) User table (t_user),
b) Role table (t_role),
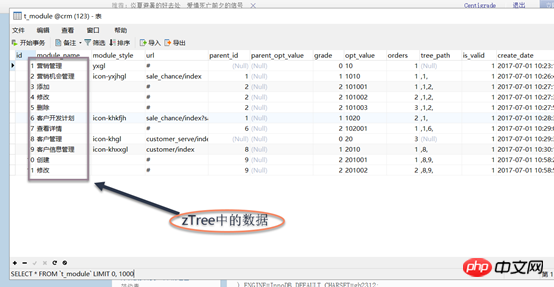
c) Resource table (t_module),
2. Two intermediate tables
a) User role table (t_user_role),
b) Role-resource table (t_permission),
3. Implementation of permission management
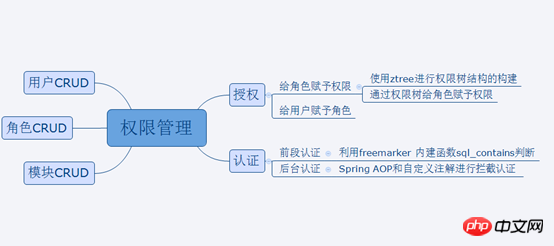
1. Module , role, user's single table CRUD
Module CRUD: operate t_module table
Role CRUD: operate t_role table
User CRUD: Operation t_role table
2. Authorization
Grant permissions to roles
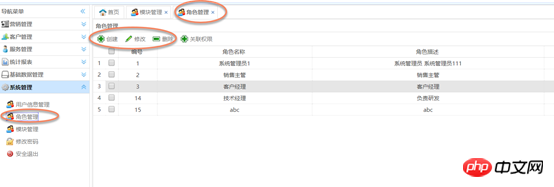
Grant permissions to roles: Use ZTREE for the construction of the permissions tree structure
# A) Awarded permissions
1, first bind this module;
## 2, bind the parent module; ## 3. Bind sub-module b) Delete permissions 1. Delete this module first; , Delete the parent module (determine whether the parent module has other sub-module associated word roles, if not, cancel it, if there is, associate it) a) Use the jQuery plug-in zTree to build a resource Tree structure, the content in the tree is the data intable t_module
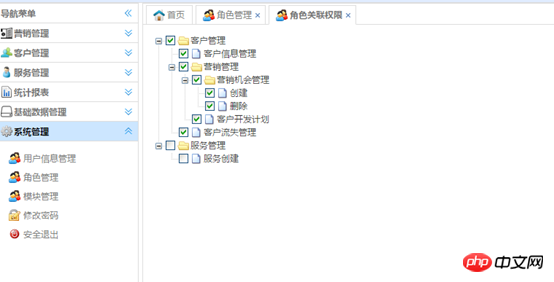 b) Use the mouse to click the selection box in zTree to operate
b) Use the mouse to click the selection box in zTree to operate
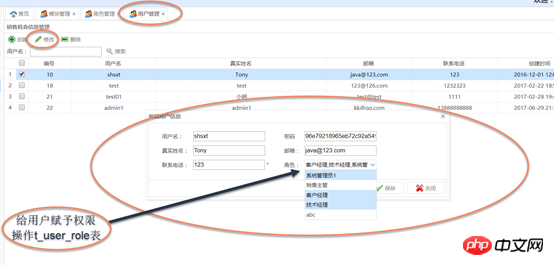
Assign roles to users Assign roles to users: Use the combobox multi-select
a). Add an account: Go directly to t_user_role insert record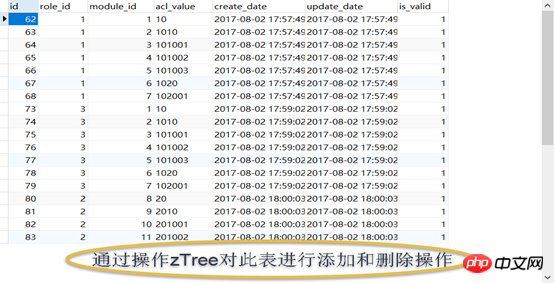
When creating a user or modifying user information, you can use the combobox multi-select box to assign role operations to the user t_user_role (user role table)
3. Authentication
Ideas:
From the t_permission table Obtain the permission value (acl_value) from the page and compare it with the value passed by the page or with the permission value specified in the annotation. Two ideas are provided below:
1. The page passes Request.getParameter("permission"); Query the permission list found in the database based on userId contains
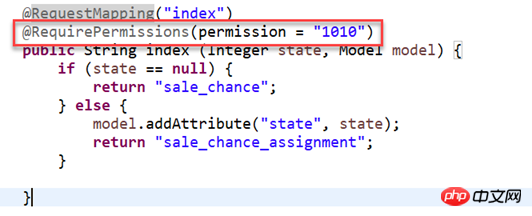
2. Clarify the module permission value through annotations: @requirePermission(permission="1010";
Backend authentication: Spring AOP and custom annotations Implement authentication
Obtain user permissions and store them in the session. Then when the user operates a resource, the permission value of a resource will be submitted to determine whether the user has this permission
Use Spring AOP for interception authentication
1: Open the annotation driver & lt; AOP: Aspectj-AutoProxy /& GT;
## Step 2: Create a proxy class @Aspect @component Step 3: Define a pointcut @Pointcut(" *execution('com.shsxt.controller.*.*((..))')") public void pointcut() {}4: Writing a enhancement: @Around (Value = "POINTCUT ()")
## 1. Determine whether the user logs in
2. #3. Save the permissions into session-"to the front page page to judge
4. The permissions of the background
5. Back to
Custom annotations
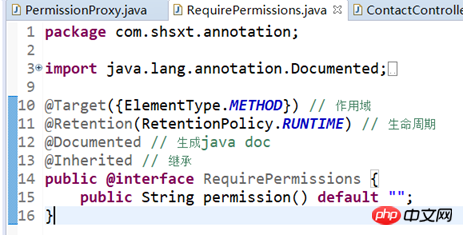 Define the entry point point : Self-interception method with permission annotations can improve performance
Define the entry point point : Self-interception method with permission annotations can improve performance
//@Pointcut("execution(* com.shsxt.controller.*.*(..))")
@Pointcut("@annotation(com.shsxt.annotation.RequirePermissions)")
public void pointcut() {
}Implemented by passing permission parameters through the front desk:
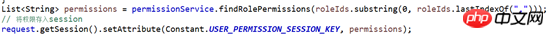
List<String> permissions = permissionService.findRolePermissions(roleIds.substring(0, roleIds.lastIndexOf(",")));
String permissioFront = request.getParameter("permission"); // 后台权限认证
AssertUtil.isTrue(!permissions.contains(permissioFront), "您无权操作此模块");Implemented through annotations
List<String> permissions = permissionService.findRolePermissions(roleIds.substring(0, roleIds.lastIndexOf(",")));
if (requirePermissions != null) {
String permission = requirePermissions.permission(); // 后台权限认证
throw new UnAuthPermissionException(permission, "您无权操作此模块");
}
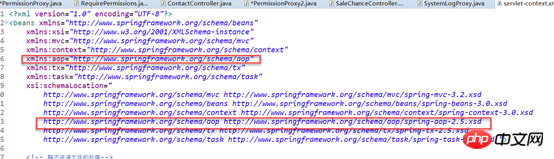
3. Introduce AOP namepsace and enable the AOP annotation driver
<!-- 启用@Aspect注解 --> <aop:aspectj-autoproxy />
 Front-end authentication: Freemarker built-in function judgment
Front-end authentication: Freemarker built-in function judgment
Use freemarker in the front-end freemarker after obtaining user permissions Grammar to determine whether the user can operate this resource (list?seq_contains('permission value'))
1.SQL:
SELECT
DISTINCT p.acl_value
FROM
t_permission p
-- LEFT JOIN t_role r ON r.id = ur.role_id
left JOIN t_user_role ur on p.role_id = ur.role_id
WHERE
ur.user_id = 10;2. Query permission in the AOP aspect class to retrieve the permission value list , put into Session
3. Front page judgment: Explanation: Use the freemarker built-in function sql_contains to judge whether the sequence contains parameter values, and return true if included is similar Collection hashmap.contains(value);
in java
The above is the detailed content of Java authorization and authentication. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1666
1666
 14
14
 1425
1425
 52
52
 1327
1327
 25
25
 1273
1273
 29
29
 1252
1252
 24
24
 Break or return from Java 8 stream forEach?
Feb 07, 2025 pm 12:09 PM
Break or return from Java 8 stream forEach?
Feb 07, 2025 pm 12:09 PM
Java 8 introduces the Stream API, providing a powerful and expressive way to process data collections. However, a common question when using Stream is: How to break or return from a forEach operation? Traditional loops allow for early interruption or return, but Stream's forEach method does not directly support this method. This article will explain the reasons and explore alternative methods for implementing premature termination in Stream processing systems. Further reading: Java Stream API improvements Understand Stream forEach The forEach method is a terminal operation that performs one operation on each element in the Stream. Its design intention is
 PHP: A Key Language for Web Development
Apr 13, 2025 am 12:08 AM
PHP: A Key Language for Web Development
Apr 13, 2025 am 12:08 AM
PHP is a scripting language widely used on the server side, especially suitable for web development. 1.PHP can embed HTML, process HTTP requests and responses, and supports a variety of databases. 2.PHP is used to generate dynamic web content, process form data, access databases, etc., with strong community support and open source resources. 3. PHP is an interpreted language, and the execution process includes lexical analysis, grammatical analysis, compilation and execution. 4.PHP can be combined with MySQL for advanced applications such as user registration systems. 5. When debugging PHP, you can use functions such as error_reporting() and var_dump(). 6. Optimize PHP code to use caching mechanisms, optimize database queries and use built-in functions. 7
 PHP vs. Python: Understanding the Differences
Apr 11, 2025 am 12:15 AM
PHP vs. Python: Understanding the Differences
Apr 11, 2025 am 12:15 AM
PHP and Python each have their own advantages, and the choice should be based on project requirements. 1.PHP is suitable for web development, with simple syntax and high execution efficiency. 2. Python is suitable for data science and machine learning, with concise syntax and rich libraries.
 PHP vs. Other Languages: A Comparison
Apr 13, 2025 am 12:19 AM
PHP vs. Other Languages: A Comparison
Apr 13, 2025 am 12:19 AM
PHP is suitable for web development, especially in rapid development and processing dynamic content, but is not good at data science and enterprise-level applications. Compared with Python, PHP has more advantages in web development, but is not as good as Python in the field of data science; compared with Java, PHP performs worse in enterprise-level applications, but is more flexible in web development; compared with JavaScript, PHP is more concise in back-end development, but is not as good as JavaScript in front-end development.
 PHP vs. Python: Core Features and Functionality
Apr 13, 2025 am 12:16 AM
PHP vs. Python: Core Features and Functionality
Apr 13, 2025 am 12:16 AM
PHP and Python each have their own advantages and are suitable for different scenarios. 1.PHP is suitable for web development and provides built-in web servers and rich function libraries. 2. Python is suitable for data science and machine learning, with concise syntax and a powerful standard library. When choosing, it should be decided based on project requirements.
 PHP's Impact: Web Development and Beyond
Apr 18, 2025 am 12:10 AM
PHP's Impact: Web Development and Beyond
Apr 18, 2025 am 12:10 AM
PHPhassignificantlyimpactedwebdevelopmentandextendsbeyondit.1)ItpowersmajorplatformslikeWordPressandexcelsindatabaseinteractions.2)PHP'sadaptabilityallowsittoscaleforlargeapplicationsusingframeworkslikeLaravel.3)Beyondweb,PHPisusedincommand-linescrip
 PHP: The Foundation of Many Websites
Apr 13, 2025 am 12:07 AM
PHP: The Foundation of Many Websites
Apr 13, 2025 am 12:07 AM
The reasons why PHP is the preferred technology stack for many websites include its ease of use, strong community support, and widespread use. 1) Easy to learn and use, suitable for beginners. 2) Have a huge developer community and rich resources. 3) Widely used in WordPress, Drupal and other platforms. 4) Integrate tightly with web servers to simplify development deployment.
 PHP vs. Python: Use Cases and Applications
Apr 17, 2025 am 12:23 AM
PHP vs. Python: Use Cases and Applications
Apr 17, 2025 am 12:23 AM
PHP is suitable for web development and content management systems, and Python is suitable for data science, machine learning and automation scripts. 1.PHP performs well in building fast and scalable websites and applications and is commonly used in CMS such as WordPress. 2. Python has performed outstandingly in the fields of data science and machine learning, with rich libraries such as NumPy and TensorFlow.




