 Java
Java
 javaTutorial
javaTutorial
 Detailed explanation of Java implementation of symmetric encryption (DES, 3DES, AES)
Detailed explanation of Java implementation of symmetric encryption (DES, 3DES, AES)
Detailed explanation of Java implementation of symmetric encryption (DES, 3DES, AES)
There are two sentences that say this:
1) Algorithms and data structures are an important part of programming. If you lose algorithms and data structures, you will lose everything. .
2) Programming is algorithms and data structures. Algorithms and data structures are the soul of programming.
Note, this is not what I said. It was summarized by countless programmers. What I said is very practical and insightful. If you want long-term sustainable development, it is still necessary to study more algorithms. Today I will tell you about the symmetric encryption algorithm among encryption algorithms, and I will teach you how to program and use the symmetric encryption algorithm here. It includes the programming and use of three symmetric encryption algorithms: DES, 3DES and AES, and is full of useful information.
1. Symmetric cryptographic algorithm
The symmetric cryptographic algorithm is the most widely used and most frequently used encryption algorithm today. It is not only used in the software industry, but is also popular in the hardware industry. Whenever security requirements are involved in various infrastructures, symmetric encryption algorithms will be given priority.
The encryption key and decryption key of the symmetric cryptographic algorithm are the same. For most symmetric cryptographic algorithms, the encryption and decryption processes are reversed.
(1) Encryption and decryption communication model
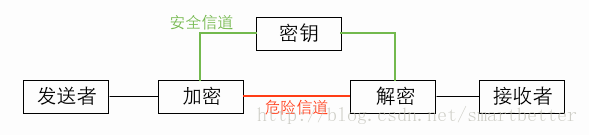
#(2) Features: open algorithm, small amount of calculation, fast encryption speed, high encryption efficiency
(3) Weakness: Both parties use the same key, and security cannot be guaranteed
There are two types of symmetric ciphers: stream ciphers and block ciphers, but block ciphers are commonly used now:
(4) Block cipher working mode
1) ECB: Electronic codebook (the most commonly used, each encryption generates an independent ciphertext group, and will not affect other ciphertext groups , that is, the same ciphertext will be generated after the same plaintext is encrypted)
2) CBC: Ciphertext link (commonly used, before plaintext encryption needs to be XORed with the previous ciphertext, also That is, the same plaintext is encrypted to produce different ciphertext)
In addition to these two commonly used working modes, there are also:
3) CFB: Ciphertext Feedback
4) OFB: Output feedback
5) CTR: Counter
These five working modes are mainly used by algorithms in cryptography when performing derivation calculations Arrived.
6. Block cipher padding method
1) NoPadding: No padding
2) PKCS5Padding:
3) ISO10126Padding:
7. Commonly used symmetric passwords:
1) DES (Data Encryption Standard, data encryption standard)
2) 3DES (Triple DES, DESede , an algorithm that performs triple DES encryption)
3) AES (Advanced Encryption Standard, advanced data encryption standard, the AES algorithm can effectively resist the attack algorithm against DES)
Let’s take a look at this first A simple comparison of the three algorithms:
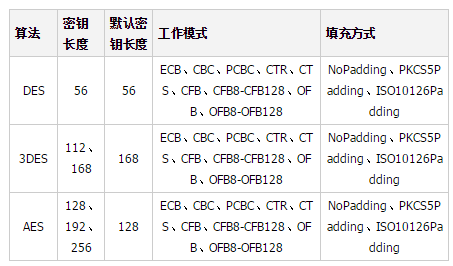
Let’s see how to use the three algorithms DES / 3DES / AES to achieve symmetric encryption:
2.DES algorithm
1.DES: Data encryption standard, a typical algorithm in the field of symmetric encryption algorithms
2. Features: short key (56 bits), short life cycle (to avoid being Crack)
3.Java implementation
1) Generate key
KeyGenerator keyGen = KeyGenerator.getInstance("DES");//密钥生成器
keyGen.init(56);//初始化密钥生成器
SecretKey secretKey = keyGen.generateKey();//生成密钥
byte[] key = secretKey.getEncoded();//密钥字节数组
2) Encryption
SecretKey secretKey = new SecretKeySpec(key, "DES");//恢复密钥
Cipher cipher = Cipher.getInstance("DES");//Cipher完成加密或解密工作类
cipher.init(Cipher.ENCRYPT_MODE, secretKey);//对Cipher初始化,加密模式
byte[] cipherByte = cipher.doFinal(data);//加密data
3) Decryption
SecretKey secretKey = new SecretKeySpec(key, "DES");//恢复密钥
Cipher cipher = Cipher.getInstance("DES");//Cipher完成加密或解密工作类
cipher.init(Cipher.DECRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//解密data
We can find that we just set different settings for encryption and decryption It's just a pattern.
3.3DES algorithm
1.3DES: Increase the key length to 112 bits or 168 bits, and improve security by increasing the number of iterations
2. Disadvantages: The processing speed is slow, the key calculation time is long, and the encryption efficiency is not high
3.Java implementation
1) Generate key
KeyGenerator keyGen = KeyGenerator.getInstance("DESede");//密钥生成器
keyGen.init(168); //可指定密钥长度为112或168,默认为168
SecretKey secretKey = keyGen.generateKey();//生成密钥
byte[] key = secretKey.getEncoded();//密钥字节数组
2) 3DES encryption
SecretKey secretKey = new SecretKeySpec(key, "DESede");//恢复密钥
Cipher cipher = Cipher.getInstance("DESede");//Cipher完成加密或解密工作类
cipher.init(Cipher.ENCRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//加密data
3) 3DES decryption
SecretKey secretKey = new SecretKeySpec(key, "DESede");//恢复密钥
Cipher cipher = Cipher.getInstance("DESede");//Cipher完成加密或解密工作类
cipher.init(Cipher.DECRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//解密data
4.AES algorithm (recommended)
1.AES: Advanced Data Encryption Standard, which can effectively resist all known attacks against the DES algorithm
2 .Features: short key establishment time, good sensitivity, low memory requirements, high security
3.Java implementation
1) Generate key
KeyGenerator keyGen = KeyGenerator.getInstance("AES");//密钥生成器
keygen.init(128); //默认128,获得无政策权限后可为192或256
SecretKey secretKey = keyGen.generateKey();//生成密钥
byte[] key = secretKey.getEncoded();//密钥字节数组
2) AES encryption
SecretKey secretKey = new SecretKeySpec(key, "AES");//恢复密钥
Cipher cipher = Cipher.getInstance("AES");//Cipher完成加密或解密工作类
cipher.init(Cipher.ENCRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//加密data##3) AES decryption
SecretKey secretKey = new SecretKeySpec(key, "AES");//恢复密钥
Cipher cipher = Cipher.getInstance("AES");//Cipher完成加密或解密工作类
cipher.init(Cipher.DECRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//解密dataFor the convenience of use, I have written tool classes for the three algorithms DES/3DES/AES. Address: Download address (new DES/3DES/AES tool class). That’s it, DES/3DES/AES three algorithms implement symmetric encryption. I hope it will be helpful to everyone's learning, and I also hope that everyone will support the PHP Chinese website. For more detailed explanations of Java implementation of symmetric encryption (DES, 3DES, AES), please pay attention to the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1663
1663
 14
14
 1420
1420
 52
52
 1313
1313
 25
25
 1266
1266
 29
29
 1239
1239
 24
24
 Is the company's security software causing the application to fail to run? How to troubleshoot and solve it?
Apr 19, 2025 pm 04:51 PM
Is the company's security software causing the application to fail to run? How to troubleshoot and solve it?
Apr 19, 2025 pm 04:51 PM
Troubleshooting and solutions to the company's security software that causes some applications to not function properly. Many companies will deploy security software in order to ensure internal network security. ...
 How do I convert names to numbers to implement sorting and maintain consistency in groups?
Apr 19, 2025 pm 11:30 PM
How do I convert names to numbers to implement sorting and maintain consistency in groups?
Apr 19, 2025 pm 11:30 PM
Solutions to convert names to numbers to implement sorting In many application scenarios, users may need to sort in groups, especially in one...
 How to simplify field mapping issues in system docking using MapStruct?
Apr 19, 2025 pm 06:21 PM
How to simplify field mapping issues in system docking using MapStruct?
Apr 19, 2025 pm 06:21 PM
Field mapping processing in system docking often encounters a difficult problem when performing system docking: how to effectively map the interface fields of system A...
 How does IntelliJ IDEA identify the port number of a Spring Boot project without outputting a log?
Apr 19, 2025 pm 11:45 PM
How does IntelliJ IDEA identify the port number of a Spring Boot project without outputting a log?
Apr 19, 2025 pm 11:45 PM
Start Spring using IntelliJIDEAUltimate version...
 How to elegantly obtain entity class variable names to build database query conditions?
Apr 19, 2025 pm 11:42 PM
How to elegantly obtain entity class variable names to build database query conditions?
Apr 19, 2025 pm 11:42 PM
When using MyBatis-Plus or other ORM frameworks for database operations, it is often necessary to construct query conditions based on the attribute name of the entity class. If you manually every time...
 How to safely convert Java objects to arrays?
Apr 19, 2025 pm 11:33 PM
How to safely convert Java objects to arrays?
Apr 19, 2025 pm 11:33 PM
Conversion of Java Objects and Arrays: In-depth discussion of the risks and correct methods of cast type conversion Many Java beginners will encounter the conversion of an object into an array...
 E-commerce platform SKU and SPU database design: How to take into account both user-defined attributes and attributeless products?
Apr 19, 2025 pm 11:27 PM
E-commerce platform SKU and SPU database design: How to take into account both user-defined attributes and attributeless products?
Apr 19, 2025 pm 11:27 PM
Detailed explanation of the design of SKU and SPU tables on e-commerce platforms This article will discuss the database design issues of SKU and SPU in e-commerce platforms, especially how to deal with user-defined sales...
 How to use the Redis cache solution to efficiently realize the requirements of product ranking list?
Apr 19, 2025 pm 11:36 PM
How to use the Redis cache solution to efficiently realize the requirements of product ranking list?
Apr 19, 2025 pm 11:36 PM
How does the Redis caching solution realize the requirements of product ranking list? During the development process, we often need to deal with the requirements of rankings, such as displaying a...



