 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 PHP md5 encryption and decryption algorithms and tools (with code)
PHP md5 encryption and decryption algorithms and tools (with code)
PHP md5 encryption and decryption algorithms and tools (with code)
The example in this article describes the encryption and decryption method implemented by php md5. The MD5 algorithm is generally used in situations where data is encrypted, such as user login passwords for websites. Students who are interested in MD5 can refer to it.
1. What is MD5?
Message Digest Algorithm MD5 (Chinese called Message Digest Algorithm Version 5) is a hash function widely used in the field of computer security to provide message integrity protection. Currently, user passwords in PHP website development are encrypted using MD5.
Second.md5 encryption algorithm code
//加密 <body style="color:green;font-size:28px;background:black;font-family:Verdana, sans-serif;"> <?php error_reporting(0);?> <form name="c" action="<?php echo $_SERVER['PHP_SELF'];?>" method="get"> Input your text: <input type="text" name="c" /> <button type="submit" value="Submit" style="color:green;font-size:28px;background:black;">Creat!</button> </form> </body> <?php //hash encode: if($c=$_GET['c'])echo 'Roger!Your MD5 code is:<br>'.md5($c).'(32bit)<br>'.substr(md5($c),8,16).'(16bit)';//截取8到24就是16位的hash,便于储存 ?>
Can 3.md5 be decrypted or cracked?
The encryption algorithm of MD5 is an irreversible encryption algorithm and cannot be decrypted in theory. The encryption principle of MD5 is a hash algorithm, which is also called a hash algorithm. The data structure of computer majors includes the knowledge of hash tables. For example, if 10 is divided by 3, the remainder is one, and if 4 is divided by 3, the remainder is also one, but if the remainder is one, you don’t know which number it is. So md5 cannot be decrypted. Even the person who designed this encryption algorithm doesn’t know. But how is your password verified? This is because the same password must be the same after encryption. You will know whether your password is correct only after you enter the password and encrypt it. In other words, only you know your password. This is also the reason why the QQ password can only be reset but not retrieved. (Reference: Can php md5 encryption be cracked? )
But if a simple MD5 password is used, it can still be cracked by brute force. They do this by continuously saving various codes and passwords and then matching them to finally get the password. However, complex passwords are still a bit difficult. (php md5 decryption code sharing (with interface, available for personal testing) )
Four. Reset password method through MD5
Since the MD5 encryption algorithm is an irreversible encryption algorithm, when you forget If the password is lost, you can reset the password or overwrite the password. For example, if you forget the website backend password, you can use php Chinese websiteMD5 online encryption tool to enter the password you want to encrypt, then generate an MD5 ciphertext string, and overwrite this ciphertext string in the original database user table. MD5 ciphertext is enough.
The above introduces the encryption method implemented by PHP md5, including the relevant content of md5 decryption. I hope it will be helpful to friends on the PHP Chinese website.
Related articles:
Can php md5 be decrypted?

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Revealing the causes of HTTP status code 460
Feb 19, 2024 pm 08:30 PM
Revealing the causes of HTTP status code 460
Feb 19, 2024 pm 08:30 PM
Decrypting HTTP status code 460: Why does this error occur? Introduction: In daily network use, we often encounter various error prompts, including HTTP status codes. These status codes are a mechanism defined by the HTTP protocol to indicate the processing of a request. Among these status codes, there is a relatively rare error code, namely 460. This article will delve into this error code and explain why this error occurs. Definition of HTTP status code 460: First, we need to understand the basics of HTTP status code
 PHP calculates MD5 hash of file
Mar 21, 2024 pm 01:42 PM
PHP calculates MD5 hash of file
Mar 21, 2024 pm 01:42 PM
This article will explain in detail about PHP calculating the MD5 hash of files. The editor thinks it is quite practical, so I share it with you as a reference. I hope you can gain something after reading this article. PHP calculates the MD5 hash of a file MD5 (MessageDigest5) is a one-way encryption algorithm that converts messages of arbitrary length into a fixed-length 128-bit hash value. It is widely used to ensure file integrity, verify data authenticity and create digital signatures. Calculating the MD5 hash of a file in PHP PHP provides multiple methods to calculate the MD5 hash of a file: Use the md5_file() function. The md5_file() function directly calculates the MD5 hash value of the file and returns a 32-character
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
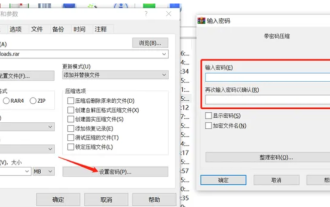 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 How to set up word decryption
Mar 20, 2024 pm 04:36 PM
How to set up word decryption
Mar 20, 2024 pm 04:36 PM
In today's work environment, everyone's awareness of confidentiality is getting stronger and stronger, and encryption operations are often performed to protect files when using software. Especially for key documents, the awareness of confidentiality should be increased, and the security of documents should be given top priority at all times. So I don’t know how well everyone understands word decryption. How to operate it specifically? Today we will actually show you the process of word decryption through the explanation below. Friends who need to learn word decryption knowledge should not miss today's course. A decryption operation is first required to protect the file, which means that the file is processed as a protective document. After doing this to a file, a prompt pops up when you open the file again. The way to decrypt the file is to enter the password, so you can directly
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 Analog, a new project by crypto veterans: raised $16 million, with airdrop expected
Feb 22, 2024 pm 04:50 PM
Analog, a new project by crypto veterans: raised $16 million, with airdrop expected
Feb 22, 2024 pm 04:50 PM
Original author: Meteor, ChainCatcher Original editor: Marco, ChainCatcher Recently, the full-chain interoperability protocol Analog has entered the public eye with the disclosure of US$16 million in financing. Investment institutions include TribeCapital, NGCVentures, Wintermute, GSR, NEAR, OrangeDAO, and Mike Novogratz’s Alternative asset management companies Samara Asset Group, Balaji Srinivasan, etc. At the end of 2023, Analog caused some excitement in the industry. They released information on the open testnet registration event on the X platform.
 How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to de-encrypt videos on EZVIZ Cloud: There are many ways to de-encrypt videos on EZVIZ Cloud, one of which is by using the EZVIZ Cloud Mobile App. Users only need to enter the device list, select the camera to be decrypted and enter the device details page. On the device details page, find the "Settings" option, and then select "Video Encryption" to make relevant settings. In the video encryption settings interface, you can choose the option to turn off video encryption, and save the settings to complete the decryption operation. This simple step allows users to easily decrypt videos and improves the convenience of using the camera. If you use the computer client of EZVIZ Cloud, you can also cancel video encryption through similar steps. Just log in and select the corresponding camera, enter the device details interface, and then look for video addition in the settings.





