AI And Cybersecurity: The New Administration's 100-Day Reckoning
At the RSAC 2025 conference this week, Snyk hosted a timely panel titled “The First 100 Days: How AI, Policy & Cybersecurity Collide,” featuring an all-star lineup: Jen Easterly, former CISA Director; Nicole Perlroth, former journalist and partner with Ballistic Ventures; Sumit Dhawan, CEO of Proofpoint; and Peter McKay, CEO of Snyk. Moderated by Axios cybersecurity reporter Sam Sabin, the conversation examined the early signs of disruption and dysfunction—and what it all means for software security, national defense, and innovation.
The discussion was grounded in new findings from a Snyk-commissioned CISO survey, which revealed stark concerns about AI-generated threats, fragmented regulation, and eroding trust between the public and private sectors.

A Surge of AI-Driven Attacks—and a Growing Crisis of Trust
Since January, 70% of surveyed CISOs reported experiencing a cyberattack involving AI. Panelists noted that organizations are rapidly embracing AI to increase productivity, but often without properly considering security implications.
This rush to adopt AI is creating a widening gap between innovation and risk management. At the same time, nearly all CISOs surveyed expressed concern that AI-generated code may be introducing hidden vulnerabilities, suggesting a dangerous disconnect between perceived readiness and the evolving threat landscape.
Peter McKay observed, “Everybody is just focused on productivity... just get the benefits of AI and we’ll figure out security later,” highlighting the widespread rush to adopt AI tools without sufficient safeguards.
Regulatory Uncertainty and Talent Flight Undermine National Security
The panel addressed the impact of federal workforce reductions and policy reversals, including the rollback of Biden-era AI executive orders. Former CISA Director Jen Easterly described the loss of technical talent from government agencies as damaging to national cyber readiness.
The panelists noted that reported loyalty requirements for federal cybersecurity personnel could further erode morale and independence. Concerns also extended to international partnerships, with reports that allied nations are beginning to limit intelligence sharing with the U.S., reflecting declining trust in the current administration.
Developers Are Racing Ahead of the Guardrails
AI is drastically accelerating software development cycles, but this rapid pace is straining traditional security frameworks. Panelists highlighted how internal pressure to innovate often overrides caution, leading to insufficiently vetted tools and code.
They stressed the importance of integrating security from the outset rather than as an afterthought, and called for secure-by-design practices to become standard. Without these safeguards, AI tools that can prevent threats may also be exploited to cause harm.
Public-Private Collaboration at Risk
Speakers emphasized that recent setbacks in federal cybersecurity leadership and policy risk reversing years of progress in public-private cooperation. The collaboration that once enabled a strong collective response to cyber threats—most notably in Ukraine—is now showing signs of strain.
Reflecting on current limitations, Dhawan admitted, “We haven't cracked the code, and we're really hoping for that form of private, public sort of collaboration.”
Several panelists expressed concern that trust is weakening on both sides, with private companies unsure about their role in threat reporting and mitigation, and government agencies losing key channels for visibility. CISA’s partnership-enabling authorities, such as CPAC, were cited as critical tools that are currently on hold.
Policy Wish Lists from the Experts
When asked what single change they would make if given a “magic wand,” panelists offered a range of pragmatic solutions. Proposals included mandating secure-by-design standards for consumer-grade routers—long a weak link in infrastructure security—and launching a national effort to clean up the open source codebase that underpins most modern applications.
Others called for harmonized, standardized AI development regulations to prevent a patchwork of conflicting state laws. There was also strong support for a software liability regime tied to demonstrable secure development practices, as well as the use of AI to refactor legacy code written in memory-unsafe languages.
As his top policy wish, McKay advocated for a national effort to improve software security at the source: “If we all just focused on how we can just clean up open source code, we would have been in a better place.”
An Urgent Need for Coordination
A unifying theme throughout the discussion was the urgent need for coordination—across sectors, agencies, and borders. The convergence of rapid AI adoption, regulatory rollbacks, and mounting cyber threats is creating a perfect storm. Industry leaders stressed that security cannot be an afterthought, and that public trust and international cooperation hinge on transparency, integrity, and mutual accountability. The panel concluded with a call to preserve the principles of trust and collaboration that once underpinned America’s cyber defense strategy—and to ensure those values guide policy moving forward.
Easterly closed with a reflection on her time at CISA and how that should serve as a guiding light moving forward: “We built trust and catalyzed trust and collaboration, and we did it with integrity, we did it with humility, we did it with transparency, and we did it with character. And that's what you all should demand from your government.”
The above is the detailed content of AI And Cybersecurity: The New Administration's 100-Day Reckoning. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1662
1662
 14
14
 1419
1419
 52
52
 1313
1313
 25
25
 1262
1262
 29
29
 1235
1235
 24
24
 Getting Started With Meta Llama 3.2 - Analytics Vidhya
Apr 11, 2025 pm 12:04 PM
Getting Started With Meta Llama 3.2 - Analytics Vidhya
Apr 11, 2025 pm 12:04 PM
Meta's Llama 3.2: A Leap Forward in Multimodal and Mobile AI Meta recently unveiled Llama 3.2, a significant advancement in AI featuring powerful vision capabilities and lightweight text models optimized for mobile devices. Building on the success o
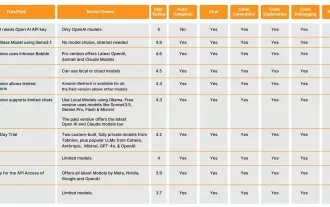 10 Generative AI Coding Extensions in VS Code You Must Explore
Apr 13, 2025 am 01:14 AM
10 Generative AI Coding Extensions in VS Code You Must Explore
Apr 13, 2025 am 01:14 AM
Hey there, Coding ninja! What coding-related tasks do you have planned for the day? Before you dive further into this blog, I want you to think about all your coding-related woes—better list those down. Done? – Let’
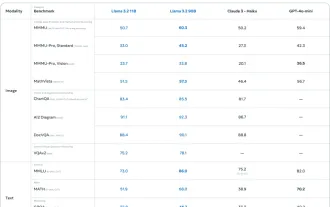 AV Bytes: Meta's Llama 3.2, Google's Gemini 1.5, and More
Apr 11, 2025 pm 12:01 PM
AV Bytes: Meta's Llama 3.2, Google's Gemini 1.5, and More
Apr 11, 2025 pm 12:01 PM
This week's AI landscape: A whirlwind of advancements, ethical considerations, and regulatory debates. Major players like OpenAI, Google, Meta, and Microsoft have unleashed a torrent of updates, from groundbreaking new models to crucial shifts in le
 Selling AI Strategy To Employees: Shopify CEO's Manifesto
Apr 10, 2025 am 11:19 AM
Selling AI Strategy To Employees: Shopify CEO's Manifesto
Apr 10, 2025 am 11:19 AM
Shopify CEO Tobi Lütke's recent memo boldly declares AI proficiency a fundamental expectation for every employee, marking a significant cultural shift within the company. This isn't a fleeting trend; it's a new operational paradigm integrated into p
 GPT-4o vs OpenAI o1: Is the New OpenAI Model Worth the Hype?
Apr 13, 2025 am 10:18 AM
GPT-4o vs OpenAI o1: Is the New OpenAI Model Worth the Hype?
Apr 13, 2025 am 10:18 AM
Introduction OpenAI has released its new model based on the much-anticipated “strawberry” architecture. This innovative model, known as o1, enhances reasoning capabilities, allowing it to think through problems mor
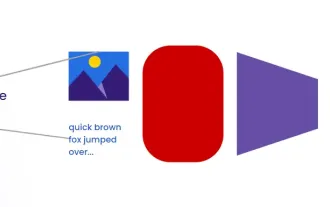 A Comprehensive Guide to Vision Language Models (VLMs)
Apr 12, 2025 am 11:58 AM
A Comprehensive Guide to Vision Language Models (VLMs)
Apr 12, 2025 am 11:58 AM
Introduction Imagine walking through an art gallery, surrounded by vivid paintings and sculptures. Now, what if you could ask each piece a question and get a meaningful answer? You might ask, “What story are you telling?
 Newest Annual Compilation Of The Best Prompt Engineering Techniques
Apr 10, 2025 am 11:22 AM
Newest Annual Compilation Of The Best Prompt Engineering Techniques
Apr 10, 2025 am 11:22 AM
For those of you who might be new to my column, I broadly explore the latest advances in AI across the board, including topics such as embodied AI, AI reasoning, high-tech breakthroughs in AI, prompt engineering, training of AI, fielding of AI, AI re
 How to Add a Column in SQL? - Analytics Vidhya
Apr 17, 2025 am 11:43 AM
How to Add a Column in SQL? - Analytics Vidhya
Apr 17, 2025 am 11:43 AM
SQL's ALTER TABLE Statement: Dynamically Adding Columns to Your Database In data management, SQL's adaptability is crucial. Need to adjust your database structure on the fly? The ALTER TABLE statement is your solution. This guide details adding colu




