 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 How to evaluate the destructive power of the website after discovering suspicious Trojan files?
How to evaluate the destructive power of the website after discovering suspicious Trojan files?
How to evaluate the destructive power of the website after discovering suspicious Trojan files?

Risk assessment and response of website Trojan files
A recent website security scan discovered suspicious PHP Trojan file, and its code snippets are as follows:
1 2 3 4 5 6 |
|
The key to this code snippet is its association with http://www.sdcshr.com/style/admin/2.txt , and the danger of the eval() function. This indicates that the Trojan file downloads and executes malicious code from the specified domain name, posing a serious security threat.
risk assessment:
The potential harm of this Trojan is extremely high, mainly reflected in the following aspects:
- Remote Code Execution (RCE): The
eval()function allows execution of arbitrary PHP code, and an attacker can remotely control the server and execute any commands. - Data Breach: Trojans may read and steal sensitive data, such as database credentials, user information, etc., and send them to attackers.
- Malware spread: The Trojan may serve as a springboard to further spread malware and infect more systems.
- Service paralysis: An attacker may use the Trojan to consume server resources or destroy system services, resulting in service interruption.
Response measures:
In view of the serious threat to the Trojan, the following measures should be taken immediately:
- Isolate infected servers: Isolate infected servers from the network immediately to prevent further spread.
- Delete Trojan files: Safely delete files containing malicious code.
- Security Audit: Perform a comprehensive security audit of the server to find other potential vulnerabilities and malware.
- System Fix: Fix all discovered vulnerabilities and enhance server security configuration.
- Password reset: Reset passwords for all server accounts, including database and FTP accounts.
- Monitor network traffic: Monitor network traffic closely to detect any suspicious activity.
- Log Analysis: Analyze server logs to understand attackers’ activities and intrusion methods.
In short, this Trojan file is extremely destructive and must be taken immediately to effectively reduce risks. It is recommended to seek help from professional security personnel for a more comprehensive safety assessment and repair work.
The above is the detailed content of How to evaluate the destructive power of the website after discovering suspicious Trojan files?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1321
1321
 25
25
 1269
1269
 29
29
 1249
1249
 24
24
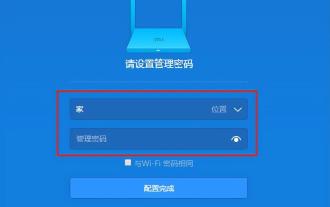 How to read Xiaomi router account and password. Detailed introduction: Introduction to Xiaomi router account and password.
May 08, 2024 pm 05:16 PM
How to read Xiaomi router account and password. Detailed introduction: Introduction to Xiaomi router account and password.
May 08, 2024 pm 05:16 PM
192.168.31.1 What is the original login password? What is the administrative password for 192.168.31.1? When I open the 192.168.31.1 login page, I am prompted to enter the management password; but I don’t know what the management password is. What should I do? 192.168.31.1 is the login IP address of the Xiaomi router. It is recommended that you set up the Xiaomi router, but when opening the 192.168.31.1 login page, you need to enter the management password. Please note that the 192.168.31.1 login page does not have a default login password. The management password that the user is prompted to enter was created by the user when setting up this Xiaomi router for the first time, as shown in the figure below. If you forget 192.168.31
 Why can't I log in to the coinbase official website?
Aug 13, 2024 pm 01:22 PM
Why can't I log in to the coinbase official website?
Aug 13, 2024 pm 01:22 PM
Having trouble logging into the Coinbase official website? Try the following steps: 1. Check the network and restart the router; 2. Check the Coinbase service status; 3. Clear browser cache and cookies; 4. Reset password; 5. Disable ad blocker; 6. Contact Coinbase support.
 What is the value and use of icp coins?
May 09, 2024 am 10:47 AM
What is the value and use of icp coins?
May 09, 2024 am 10:47 AM
As the native token of the Internet Computer (IC) protocol, ICP Coin provides a unique set of values and uses, including storing value, network governance, data storage and computing, and incentivizing node operations. ICP Coin is considered a promising cryptocurrency, with its credibility and value growing with the adoption of the IC protocol. In addition, ICP coins play an important role in the governance of the IC protocol. Coin holders can participate in voting and proposal submission, affecting the development of the protocol.
 The difference between oracle database and mysql
May 10, 2024 am 01:54 AM
The difference between oracle database and mysql
May 10, 2024 am 01:54 AM
Oracle database and MySQL are both databases based on the relational model, but Oracle is superior in terms of compatibility, scalability, data types and security; while MySQL focuses on speed and flexibility and is more suitable for small to medium-sized data sets. . ① Oracle provides a wide range of data types, ② provides advanced security features, ③ is suitable for enterprise-level applications; ① MySQL supports NoSQL data types, ② has fewer security measures, and ③ is suitable for small to medium-sized applications.
 The difference between get and post in vue
May 09, 2024 pm 03:39 PM
The difference between get and post in vue
May 09, 2024 pm 03:39 PM
In Vue.js, the main difference between GET and POST is: GET is used to retrieve data, while POST is used to create or update data. The data for a GET request is contained in the query string, while the data for a POST request is contained in the request body. GET requests are less secure because the data is visible in the URL, while POST requests are more secure.
 How to unlock the computer power-on password (easily deal with forgotten passwords)
May 07, 2024 pm 07:37 PM
How to unlock the computer power-on password (easily deal with forgotten passwords)
May 07, 2024 pm 07:37 PM
Due to various reasons, we may forget the power-on password we set, resulting in the inability to log in normally during daily use of the computer. Such a situation will cause great trouble and waste of time if we need to urgently use important files in the computer or handle urgent matters. To help you quickly unlock computer startup password protection if you forget your password, this article will introduce you to some unlocking methods to break through the computer startup password. Reset the password by restarting the computer into safe mode We can reset the password by restarting the computer into safe mode in Windows system. The system will display the option "Forgot Password" when we click this option after entering the wrong password five times in succession on the login interface. Log in with an administrator account and change the password
 How to convert XML files to PDF on your phone?
Apr 02, 2025 pm 10:12 PM
How to convert XML files to PDF on your phone?
Apr 02, 2025 pm 10:12 PM
It is impossible to complete XML to PDF conversion directly on your phone with a single application. It is necessary to use cloud services, which can be achieved through two steps: 1. Convert XML to PDF in the cloud, 2. Access or download the converted PDF file on the mobile phone.
 Sesame Open Door Exchange Web Page Login Latest version gateio official website entrance
Mar 04, 2025 pm 11:48 PM
Sesame Open Door Exchange Web Page Login Latest version gateio official website entrance
Mar 04, 2025 pm 11:48 PM
A detailed introduction to the login operation of the Sesame Open Exchange web version, including login steps and password recovery process. It also provides solutions to common problems such as login failure, unable to open the page, and unable to receive verification codes to help you log in to the platform smoothly.



