全国地区带经纬度
地区编码带经纬度 无
地区编码带经纬度
Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1321
1321
 25
25
 1269
1269
 29
29
 1249
1249
 24
24
 11 common classification feature encoding techniques
Apr 12, 2023 pm 12:16 PM
11 common classification feature encoding techniques
Apr 12, 2023 pm 12:16 PM
Machine learning algorithms only accept numerical input, so if we encounter categorical features, we will encode the categorical features. This article summarizes 11 common categorical variable encoding methods. 1. ONE HOT ENCODING The most popular and commonly used encoding method is One Hot Enoding. A single variable with n observations and d distinct values is converted into d binary variables with n observations, each binary variable is identified by a bit (0, 1). For example: the simplest implementation after coding is to use pandas' get_dummiesnew_df=pd.get_dummies(columns=[‘Sex’], data=df)2,
 How many bytes do utf8 encoded Chinese characters occupy?
Feb 21, 2023 am 11:40 AM
How many bytes do utf8 encoded Chinese characters occupy?
Feb 21, 2023 am 11:40 AM
UTF8 encoded Chinese characters occupy 3 bytes. In UTF-8 encoding, one Chinese character is equal to three bytes, and one Chinese punctuation mark occupies three bytes; while in Unicode encoding, one Chinese character (including traditional Chinese) is equal to two bytes. UTF-8 uses 1~4 bytes to encode each character. One US-ASCIl character only needs 1 byte to encode. Latin, Greek, Cyrillic, Armenian, and Hebrew with diacritical marks. , Arabic, Syriac and other letters require 2-byte encoding.
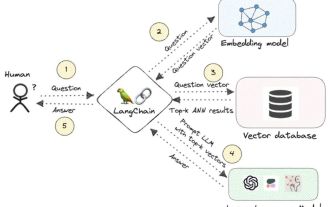 Knowledge graph: the ideal partner for large models
Jan 29, 2024 am 09:21 AM
Knowledge graph: the ideal partner for large models
Jan 29, 2024 am 09:21 AM
Large language models (LLMs) have the ability to generate smooth and coherent text, bringing new prospects to areas such as artificial intelligence conversation and creative writing. However, LLM also has some key limitations. First, their knowledge is limited to patterns recognized from training data, lacking a true understanding of the world. Second, reasoning skills are limited and cannot make logical inferences or fuse facts from multiple data sources. When faced with more complex and open-ended questions, LLM's answers may become absurd or contradictory, known as "illusions." Therefore, although LLM is very useful in some aspects, it still has certain limitations when dealing with complex problems and real-world situations. In order to bridge these gaps, retrieval-augmented generation (RAG) systems have emerged in recent years. The core idea is
 Several common encoding methods
Oct 24, 2023 am 10:09 AM
Several common encoding methods
Oct 24, 2023 am 10:09 AM
Common encoding methods include ASCII encoding, Unicode encoding, UTF-8 encoding, UTF-16 encoding, GBK encoding, etc. Detailed introduction: 1. ASCII encoding is the earliest character encoding standard, using 7-bit binary numbers to represent 128 characters, including English letters, numbers, punctuation marks, control characters, etc.; 2. Unicode encoding is a method used to represent all characters in the world The standard encoding method of characters, which assigns a unique digital code point to each character; 3. UTF-8 encoding, etc.
 PHP coding tips: How to generate a QR code with anti-counterfeiting verification function?
Aug 17, 2023 pm 02:42 PM
PHP coding tips: How to generate a QR code with anti-counterfeiting verification function?
Aug 17, 2023 pm 02:42 PM
PHP coding tips: How to generate a QR code with anti-counterfeiting verification function? With the development of e-commerce and the Internet, QR codes are increasingly used in various industries. In the process of using QR codes, in order to ensure product safety and prevent counterfeiting, it is very important to add anti-counterfeiting verification functions to the QR codes. This article will introduce how to use PHP to generate a QR code with anti-counterfeiting verification function, and attach corresponding code examples. Before starting, we need to prepare the following necessary tools and libraries: PHPQRCode: PHP
 What are the hdb3 encoding rules?
Aug 29, 2023 pm 01:38 PM
What are the hdb3 encoding rules?
Aug 29, 2023 pm 01:38 PM
The coding rules are: 1. If the previous code is 0 and the current data bit is 0, the code is 0; 2. If the previous code is 0 and the current data bit is 1, the code is bipolar pulse (+A or - A), and the counter is increased by 1; 3. If the previous code is 1 and the current data bit is 1, the code is 0, and the counter is increased by 1; 4. If the previous code is 1, the current data bit is 0, The encoding method is determined based on the parity of the counter. If it is an even number, the encoding is (+B or -B). If it is an odd number, the encoding is zero level and the counter is cleared and so on.
 Learn how to improve coding performance based on GenAI in one article
Apr 01, 2024 pm 06:49 PM
Learn how to improve coding performance based on GenAI in one article
Apr 01, 2024 pm 06:49 PM
Hellofolks, my name is Luga, and today we will talk about technologies related to the artificial intelligence (AI) ecological field - GenAI. Facing the challenges of rapid technological innovation and differentiated business scenarios, traditional coding methods have begun to become acclimated and cannot fully cope with the growing demands. At the same time, emerging general-purpose GenAI (artificial intelligence technology) has great potential to meet this demand. As a representative of artificial intelligence technology, GenAI has begun to be widely used in all walks of life with its strong potential and capabilities. It can automatically learn and adapt to coding needs in different scenarios, greatly improving coding efficiency and quality. Through deep learning and model optimization, GenAI is able to accurately understand different
 How to view longitude and latitude on Baidu Maps How to view longitude and latitude
Mar 12, 2024 pm 12:10 PM
How to view longitude and latitude on Baidu Maps How to view longitude and latitude
Mar 12, 2024 pm 12:10 PM
When we use this platform, we all know that every location has coordinates. I believe that students who have studied geography will know what the longitude and latitude coordinates are. The above functions can be said to be very powerful. Not only can you locate some of your locations in real time, but it can also let you know what the current longitude and latitude are. That is to say, we can all check the longitude and latitude coordinates of any location on the map. In this way, we can know the corresponding specific locations more accurately, but the majority of users who don’t know are still viewing it, so in order to give you a better understanding of it, let’s join the editor now Take a look, I believe you won’t miss it, come and take a look.




