锁的类型
锁的类型(Tyep列值,RID和KEY的话,表示锁在行上)有如下几种: RID=表中单个行的锁,由行标识符(RID)标识。 KEY=索引内保护可串行事务中一系列键的锁。 PAG=数据页或索引页的锁。 EXT=对某区的锁。 TAB=整个表(包括所有数据和索引)的锁。 DB=数据库的锁。 FIL
锁的类型(Tyep 列值, RID 和 KEY 的话, 表示锁在行上) 有如下几种:RID = 表中单个行的锁,由行标识符 (RID) 标识。
KEY = 索引内保护可串行事务中一系列键的锁。
PAG = 数据页或索引页的锁。
EXT = 对某区的锁。
TAB = 整个表(包括所有数据和索引)的锁。
DB = 数据库的锁。
FIL = 数据库文件的锁。
APP = 指定的应用程序资源的锁。
MD = 元数据或目录信息的锁。
HBT = 堆或 B 树索引的锁。在 SQL Server 2005 中此信息不完整。
AU = 分配单元的锁。在 SQL Server 2005 中此信息不完整。
锁的类型(Tyep 列值, RID 和 KEY 的话, 表示锁在行上) 有如下几种: RID = 表中单个行的锁,由行标识符 (RID) 标识。 KEY = 索引内保护可串行事务中一系列键的锁。 PAG = 数据页或索引页的锁。 EXT = 对某区的锁。 TAB = 整个表(包括所有数据和索引)的锁。 DB = 数据库的锁。 FIL = 数据库文件的锁。 APP = 指定的应用程序资源的锁。 MD = 元数据或目录信息的锁。 HBT = 堆或 B 树索引的锁。在 SQL Server 2005 中此信息不完整。 AU = 分配单元的锁。在 SQL Server 2005 中此信息不完整。

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1667
1667
 14
14
 1426
1426
 52
52
 1328
1328
 25
25
 1273
1273
 29
29
 1255
1255
 24
24
 What does the identity attribute in SQL mean?
Feb 19, 2024 am 11:24 AM
What does the identity attribute in SQL mean?
Feb 19, 2024 am 11:24 AM
What is Identity in SQL? Specific code examples are needed. In SQL, Identity is a special data type used to generate auto-incrementing numbers. It is often used to uniquely identify each row of data in a table. The Identity column is often used in conjunction with the primary key column to ensure that each record has a unique identifier. This article will detail how to use Identity and some practical code examples. The basic way to use Identity is to use Identit when creating a table.
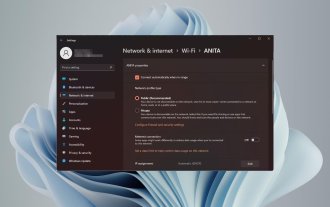 How to change network type to private or public in Windows 11
Aug 24, 2023 pm 12:37 PM
How to change network type to private or public in Windows 11
Aug 24, 2023 pm 12:37 PM
Setting up a wireless network is common, but choosing or changing the network type can be confusing, especially if you don't know the consequences. If you're looking for advice on how to change the network type from public to private or vice versa in Windows 11, read on for some helpful information. What are the different network profiles in Windows 11? Windows 11 comes with a number of network profiles, which are essentially sets of settings that can be used to configure various network connections. This is useful if you have multiple connections at home or office so you don't have to set it all up every time you connect to a new network. Private and public network profiles are two common types in Windows 11, but generally
 How SpringBoot monitors redis Key change events
May 26, 2023 pm 01:55 PM
How SpringBoot monitors redis Key change events
May 26, 2023 pm 01:55 PM
1. Function Overview Keyspace notification allows clients to receive events that modify Rediskey changes in some way by subscribing to channels or patterns. All commands that modify key keys. All keys that received the LPUSHkeyvalue[value…] command. All expired keys in the db database. Events are distributed through Redis's subscription and publishing functions (pub/sub), so all clients that support subscription and publishing functions can directly use the keyspace notification function without any modifications. Because the current subscription and publishing functions of Redis adopt a fireandforget strategy, if your program
 Implementing dynamic arrays in Python: from beginner to proficient
Apr 21, 2023 pm 12:04 PM
Implementing dynamic arrays in Python: from beginner to proficient
Apr 21, 2023 pm 12:04 PM
Part 1 Let’s talk about the nature of Python sequence types. In this blog, let’s talk about Python’s various “sequence” classes and the three built-in commonly used data structures – list, tuple and character. The nature of the string class (str). I don’t know if you have noticed it, but these classes have an obvious commonality. They can be used to save multiple data elements. The most important function is: each class supports subscript (index) access to the elements of the sequence, such as using SyntaxSeq[i]. In fact, each of the above classes is represented by a simple data structure such as an array. However, readers familiar with Python may know that these three data structures have some differences: for example, tuples and strings cannot be modified, while lists can.
 How to solve the problem of batch deletion of key values in redis
May 31, 2023 am 08:59 AM
How to solve the problem of batch deletion of key values in redis
May 31, 2023 am 08:59 AM
Problems encountered: During the development process, you will encounter keys that need to be deleted in batches according to certain rules, such as login_logID (ID is a variable). Now you need to delete data such as "login_log*", but redis itself only has batch query. Command keys for class key values, but there is no command for batch deletion of a certain class. Solution: Query first, then delete, use xargs to pass parameters (xargs can convert pipe or standard input (stdin) data into command line parameters), execute the query statement first, and then remove the queried key value and the original del parameters. delete. redis-cliKEYSkey* (search condition)|xargsr
 Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Sep 04, 2024 pm 06:32 PM
Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Sep 04, 2024 pm 06:32 PM
An unpatchable Yubico two-factor authentication key vulnerability has broken the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices. The Feitian A22 JavaCard and other devices using Infineon SLB96xx series TPMs are also vulnerable.All
 How to create a video matrix account? What types of matrix accounts do it have?
Mar 21, 2024 pm 04:57 PM
How to create a video matrix account? What types of matrix accounts do it have?
Mar 21, 2024 pm 04:57 PM
With the popularity of short video platforms, video matrix account marketing has become an emerging marketing method. By creating and managing multiple accounts on different platforms, businesses and individuals can achieve goals such as brand promotion, fan growth, and product sales. This article will discuss how to effectively use video matrix accounts and introduce different types of video matrix accounts. 1. How to create a video matrix account? To make a good video matrix account, you need to follow the following steps: First, you must clarify what the goal of your video matrix account is, whether it is for brand communication, fan growth or product sales. Having clear goals helps develop strategies accordingly. 2. Choose a platform: Choose an appropriate short video platform based on your target audience. The current mainstream short video platforms include Douyin, Kuaishou, Huoshan Video, etc.
 What is the type of return value of Golang function?
Apr 13, 2024 pm 05:42 PM
What is the type of return value of Golang function?
Apr 13, 2024 pm 05:42 PM
Go functions can return multiple values of different types. The return value type is specified in the function signature and returned through the return statement. For example, a function can return an integer and a string: funcgetDetails()(int,string). In practice, a function that calculates the area of a circle can return the area and an optional error: funccircleArea(radiusfloat64)(float64,error). Note: If the function signature does not specify a type, a null value is returned; it is recommended to use a return statement with an explicit type declaration to improve readability.




